Information Security Policy
Issued: March 1st, 2010. Minor Update: April 10, 2018
Related Policies: Employees Acceptable Use Policy, Hampshire College Data Security Policy, Hampshire College Password Policy, Hampshire College VPN Policy, Hampshire College Email Accounts Policy, Document Retention and Destruction Policy and Schedule, Hampshire College Security Breach Policy.
1.0 Purpose
This policy defines the elements and mechanisms of the information security structure at Hampshire College. It ensures that the College:
- Establishes a comprehensive approach to information security,
- Complies with federal and state regulations regarding the collection of Level III information as defined in Hampshire College's Data Security Policy. These regulations include Mass 93H/210 CMR 17, Federal Red Flag Rules, FERPA, eDiscovery as well as non-Mass state personal information laws.
- Establishes effective practices for the protection and security of information assets.
- Develops procedures for responding to breaches of information security.
2.0 Scope
This policy is intended to support the protection, control and management of Hampshire College's information assets. It covers Level III data and information (as defined in the Hampshire College Data Security Policy) that is:
- Stored on databases
- Stored on computers
- Transmitted across internal and public networks
- Printed or hand written on paper, white boards etc.
- Stored on removable media such as CD-ROMs, hard disks, tapes and other similar media
- Stored on fixed media such as hard disks and disk sub-systems
- Held on film or microfiche
- Presented on slides, overhead projectors, using visual and audio media
2.1 Components of the Security System
Hampshire College protects the security of its Level III information through integrated policies, education and training, software protection, and physical asset security. These elements represent a multifaceted approach to information security as presented below.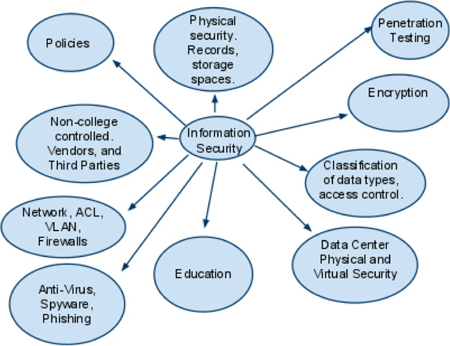
3.0 Policy
The College specifically prohibits unauthorized access to, tampering with, deliberately introducing inaccuracies to, or causing loss of Hampshire's information assets. It also prohibits using information assets to violate any law, commit an intentional breach of confidentiality or privacy, compromise the performance of systems, damage software, physical devices or networks, or otherwise sabotage College information assets.
The College protects its information assets from threats and exploits, whether internal or external, deliberate or accidental. The College recognizes that no single office, policy, or procedure provides absolute security; therefore, all College employees and authorized users of Hampshire College's information systems are responsible for minimizing risks and securing information assets within their control.
Campus-wide security awareness, training, and education and compliance with policies and procedures are vital to information security. Therefore the College will provide an information security educational program that is distributed and readily available to users. The goal of this progam is to educate users in safe and secure computing practices as well as proper handling and classification of Level III data.
The College will take appropriate action in response to misuse of College information assets. Any violation of this policy may result in legal action and/or College disciplinary action under applicable College and administrative policies and procedures up to and including termination.
The office of information technology will review the information security program annually and report the results to the vice president for finance and administration.
3.1 Policies and Procedures
The following policies and procedures provide detailed information, which together constitute Hampshire College's information security policy:
- Employees Acceptable Use Policy
- Hampshire College Data Security Policy
- Hampshire College Password Policy
- Hampshire College VPN Policy
- Hampshire College Email Accounts Policy
- Document Retention and Destruction Policy and Schedule
- Hampshire College Security Breach Policy
3.2 Access to Information and Systems
Access to Level III and/or confidential information, as defined in the Hampshire College Data Sensitivity Policy, is limited to the following groups and individuals: employees, temporary employees, third party contractors, and outside agencies, who are required to access this information to perform their job function or to fulfill contractual obligations. Third party contractors and outside agencies requesting access to this information must submit to the Director of Information Technology a written request stating why they need access to the information and a statement that they are in compliance with Mass 201 CMR 17. Exceptions to this rule are federal and state tax authorities with a need to know.
Access to Hampshire College systems and services will be limited to active users and accounts only. Users should refer to the Hampshire College Password Policy for authentication guidance. Users who attempt to access the College's information systems with expired passwords will be blocked after multiple unsuccessful attempts. Faculty or staff who have voluntarily terminated their employment may request to retain an account for up to one month after the last day of employment and have their e-mail forwarded to a non-Hampshire account for that period. Notification will be sent via email one week prior to the pending account deletion date. The employee is responsible for archiving or relocating email prior to that date.
Faculty or staff members who have been terminated involuntarily from College employment will have their accounts deleted on the last day of employment.
3.3 Systems Security Responsibilities
The Hampshire College information tyechnology department (HIT) is the "owner" of the College's information systems infrastructure, and is responsible for ensuring that network and software systems are effectively designed and maintained to provide optimal confidentiality, integrity, and availability. HIT is primarily responsible for network and operating software design and maintenance, standard software "image" configuration and maintenance, network storage, data transmission, information retrieval controls, and asset disposal. HIT develops and implements controls and processes relating to access, systems performance, systems monitoring to detect intrusion and/or malicious code, and deploying security software for these systems. HIT also assures the physical security of institutional servers, which contain access Level III data and information, through a variety of proprietary strategies.
3.4 Physical Security
3.4.1 Data Centers and Information Technology Designated Secure Areas
Designated secure areas must be locked at all times. Designated secure areas will be labeled as such by appropriate signage.
Emergency access to secure areas can be provided by the Department of Campus Safety and Wellbeing. The director of information technology, or his/her designee, will be notified of such access via telephone or email in a timely fashion. Vendors/guests (non-Hampshire employees) must be accompanied by appropriate Hampshire information technology or public safety staff while in any protected location.
3.4.2 Records Storage
Areas used to store Level III records as defined in the Hampshire College Data Security Policy should be physically secured. File cabinets and other means of storage must be locked and secured . Access to areas containing Level III materials will be provided only to authorized personnel only as outlined in section 3.2 above.
The department who owns the material in question will log access to these areas.
3.5 Data Retention and Destruction
Level III materials will be retained and destroyed in accordance with the Hampshire College Records Retention Policy. Note: This policy is outdated and is currently under review.
All Hampshire College IT Infrastructure Department systems backups are retained for 90 days.
3.6 Policy Violations
Employees who violate this policy are subject to disciplinary action, up to and including termination.
3.7 Training
All new employees of the College must participate in the on-line security awareness and training program. This program is provided as a component of the New Employee Orientation Program delivered through the office of human resources. Employees who handle Level III data as defined in the Hampshire College Data Security Policy will also be required to undergo annual security training.
3.8 Encryption of Data
All Level III data, as classified by the Hampshire College Data Security Policy, that is transmitted across public networks, including wireless, must be encrypted using standards outlined in the Hampshire College Encryption Policy.
3.9 Storage of Level III Information
Storage of Level III data as classified by the Hampshire College Data Security Policy on desktops, laptops, and portable devices is strongly discouraged. This includes but is not limited to USB sticks, portable hard drives, CD ROM, DVD or by other means of electronic data storage. This information should be stored on College servers and accessed remotely using VPN. For more information regarding VPN installation and usage please refer to Hampshire College VPN Policy. When stored locally, encryption of this information is required. Please reference the Hampshire College Data Security Policy for more information regarding data classification and encryption techniques.
3.10 Data Breach
Data breaches will be handled in accordance with the Hampshire College Security Breach Policy.

